1.2万人以上のお客様に利用されています










































データリスクは複雑な課題です。
Forcepoint Data Security Cloudで簡素化できます。
コンテキストで分類
AI Meshは、高い信頼性をもってデータの機密性を明瞭に示します。
ポリシー管理の統合
DSPM、DLP、DDR、CASB、SWGの機能を1つのプラットフォームに統合します。
あらゆる場所に適用
クラウド、ウェブ、エンドポイント、メール、ネットワーク全体に数秒でポリシーを適用します。
重要な事柄の理解
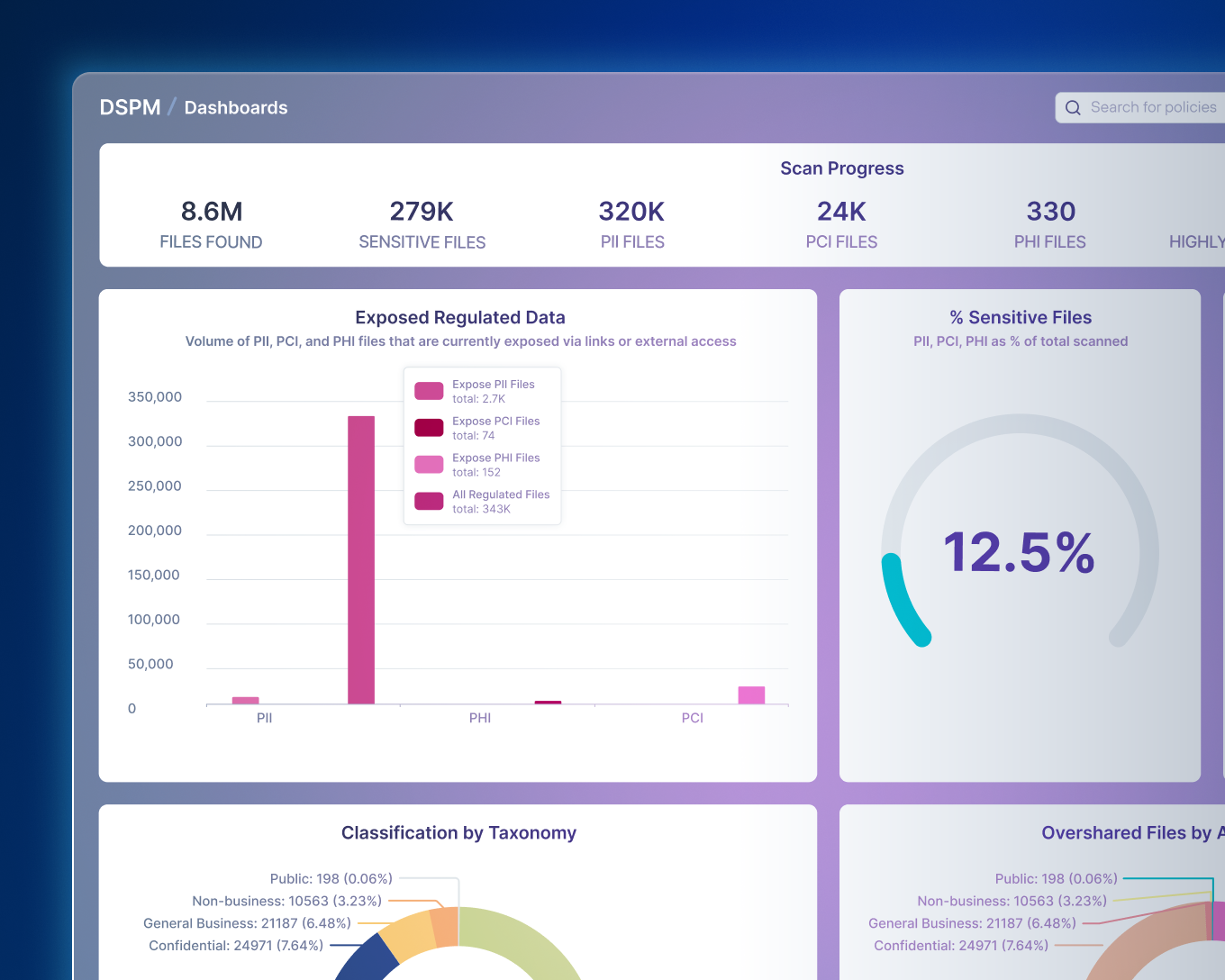
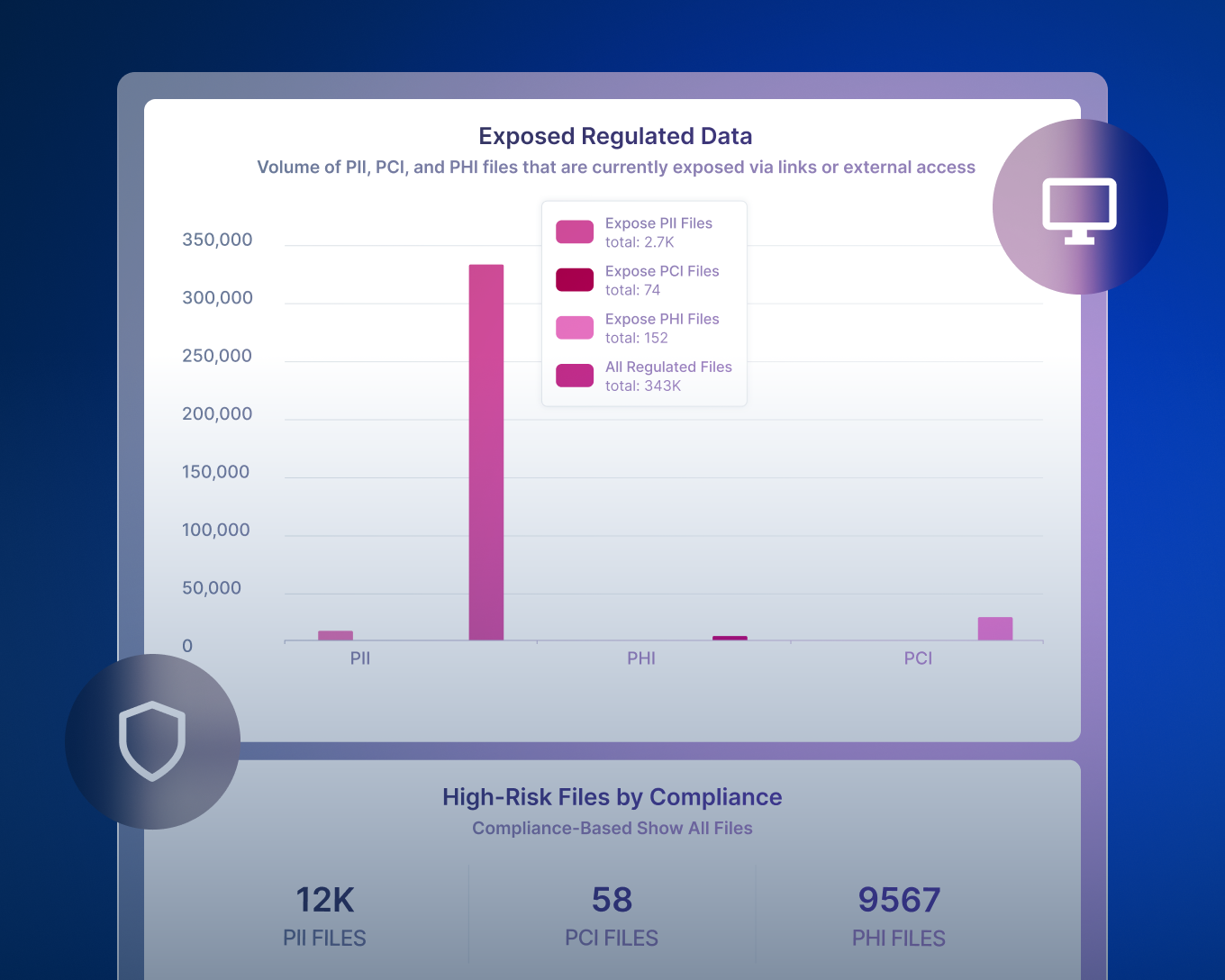
どのようなデータがあり、それがどこにあるかを探ります。
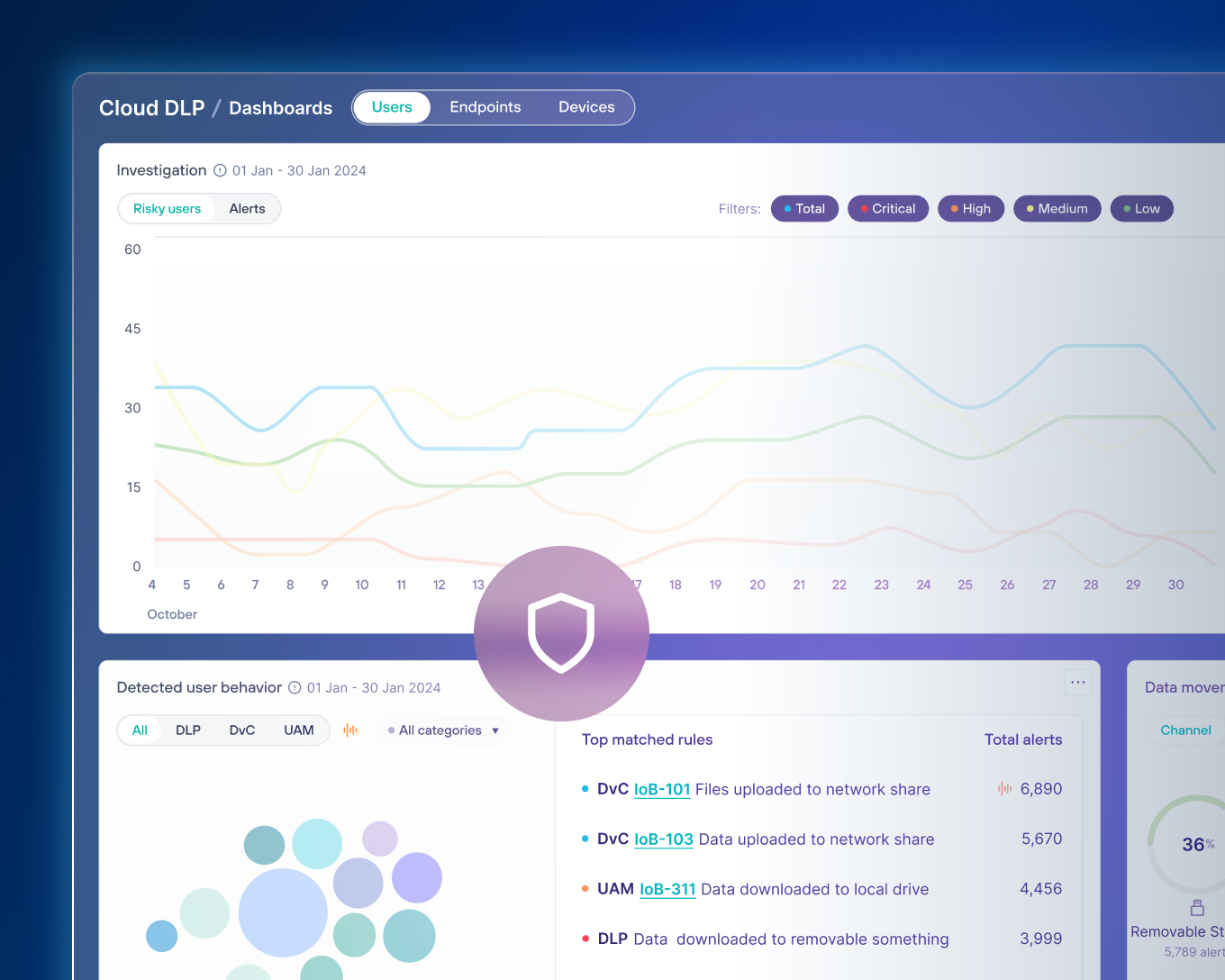
リスクに適応
脅威の出現に応じてポリシーを動的に調整します。
セキュリティを簡素化
すべてのチャネルのワークフローとポリシー制御を自動化します。
データ損失を防止してコンプライアンスを簡素化
紹介:データ検出と対応
Forcepoint Data Detection and Response(DDR)はデータを継続的に監視することで、潜在的なデータ侵害アクティビティを検出して事前に脅威を防止します。
詳細を見る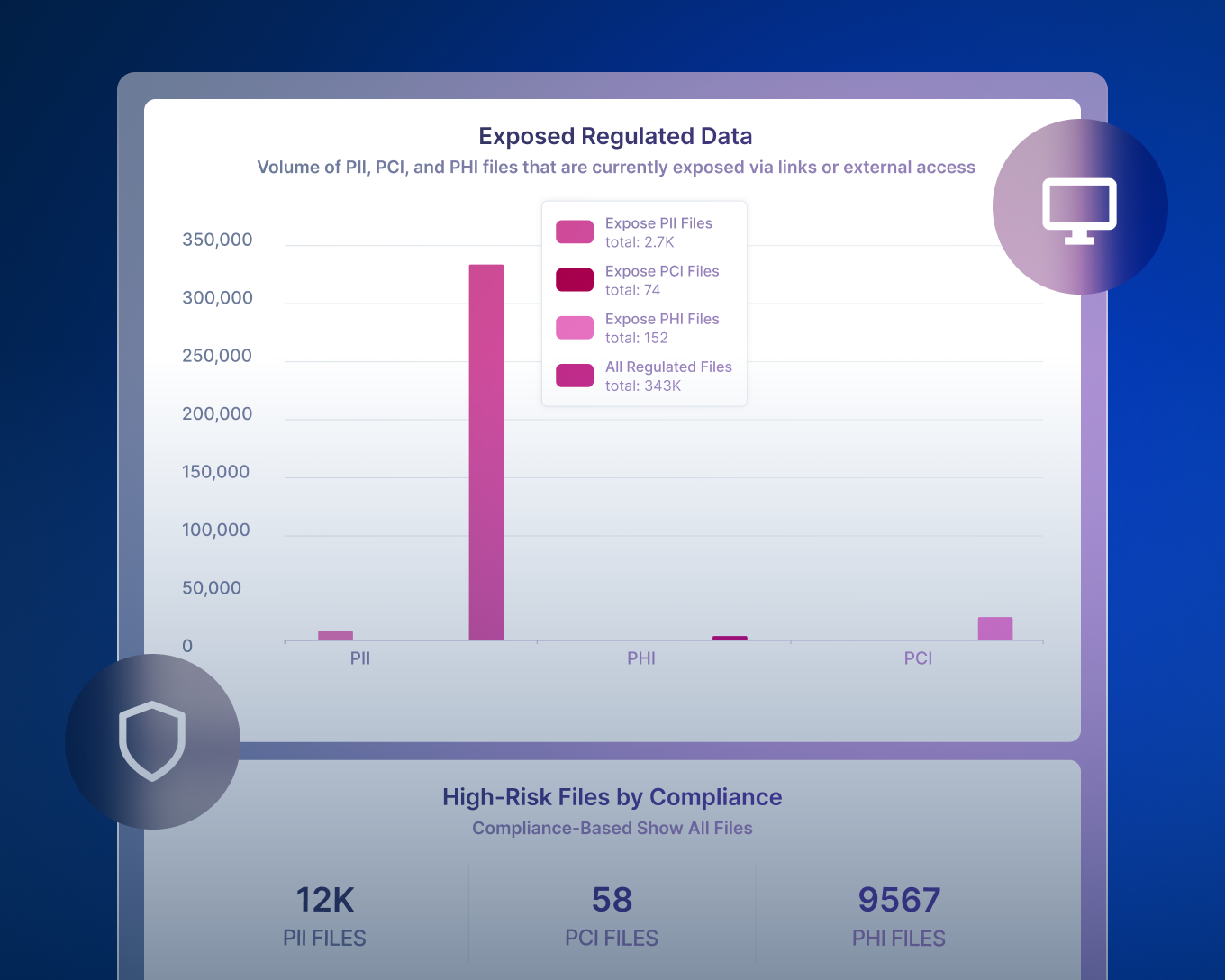
データセキュリティをビジネス上の利点に変える
データセキュリティについ
て持っておくべき知識

ガイド
AI Mesh

ガイド
DSPMのエグゼクティブガイド

EBOOK
DLP購入者ガイド

ガイド
データセキュリティに関する実務エグゼクティブガイド
データリスクアセスメントを開始する