Security Designed with
Your Mission in Mind
Secure data everywhere it goes and protect the network's edge with accredited and dependable cybersecurity solutions.
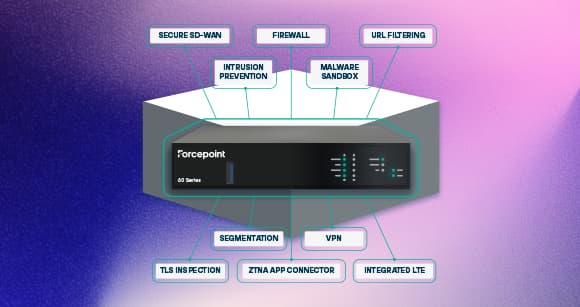
Nobody Gets In, Nothing Gets Out
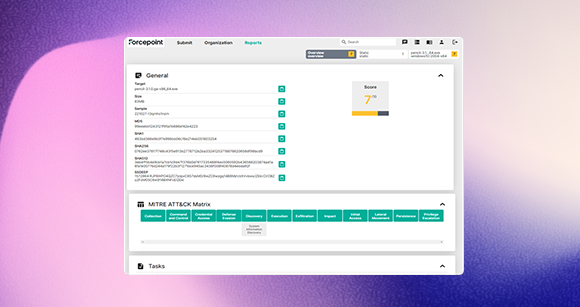
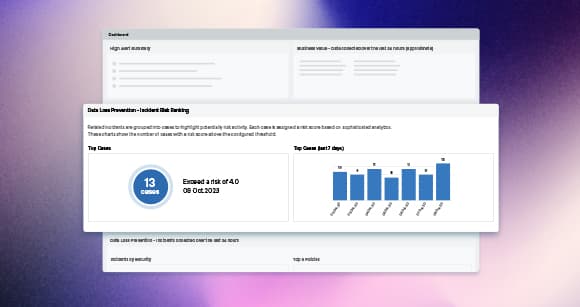
Keep threat actors at bay and data secure with DLP, DSPM, NGFW, and other cybersecurity solutions while maintaining compliance with NIST and similar frameworks.
Enforce Zero Trust and Adopt NIST
Implement NIST frameworks to manage and reduce cybersecurity risks and adhere to the Zero Trust Maturity Model to further federal modernization efforts.
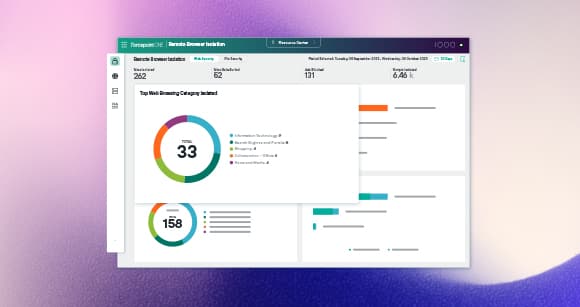
Secure Data Everywhere
Forcepoint solutions are operationally focused to meet your mission needs, whether they be tactical and on the ground or in-house at headquarters.
Frameworks, Compliance and Conformance

National Institute of Standards and Technology

Common Criteria

Cybersecurity Maturity Model Certification

Federal Information Processing Standards
Network and Data Security
Forcepoint Public Sector Products
Forcepoint Public Sector Resources