How Discovery and AI Classification Work with Forcepoint DSPM
0 min read

Tim Herr
Imagine your company retains customer invoices that include Personally Identifiable Information (PII) subject to data privacy regulations. Those invoices are stored on a secure server, and only a small number of trusted users have permission to access them. You know where your sensitive data resides, so shouldn’t you be in good shape to avoid breaches and non-compliance?
Here’s where you have to ask yourself: Do you know where else that sensitive data might be found?
Copies of these invoices, or segments of them embedded in different documents, may have been uploaded to shared network folders or stored in locations unknown to admins. Unless you can find and control all instances of this PII, you’re at serious risk of data loss and regulatory penalties.
Correctly identifying the where and what of all your data is what data discovery and classification are all about. These processes are two of the key capabilities offered by Forcepoint Data Security Posture Management (DSPM), enabling organizations to take a proactive approach to securing sensitive data and maintaining compliance. This leads to an enhanced security posture that assists complementary security solutions like Data Loss Prevention (DLP) in delivering optimum protection.
Here we’ll look at how data discovery and data classification work with Forcepoint DSPM, going over the solution’s capabilities as well as illustrating how users navigate them.
Rapidly scan files for data discovery
Data discovery often requires scanning files containing many terabytes of data. Forcepoint DSPM can scan data rapidly across diverse storage environments, including major platforms such as Amazon (AWS S3 and IAM), Microsoft (Azure AD, OneDrive, SharePoint Online) and Google (Google Drive and IAM), as well as local LDAP and SharePoint systems. With Forcepoint, customers can also run discovery scans as many times as they need to without incurring additional charges.
When performing data discovery with Forcepoint DSPM, a dashboard shows scanning progress across various cloud-based and on-premises data assets. User can also access an overview data risk assessment to understand the areas of highest data risk.
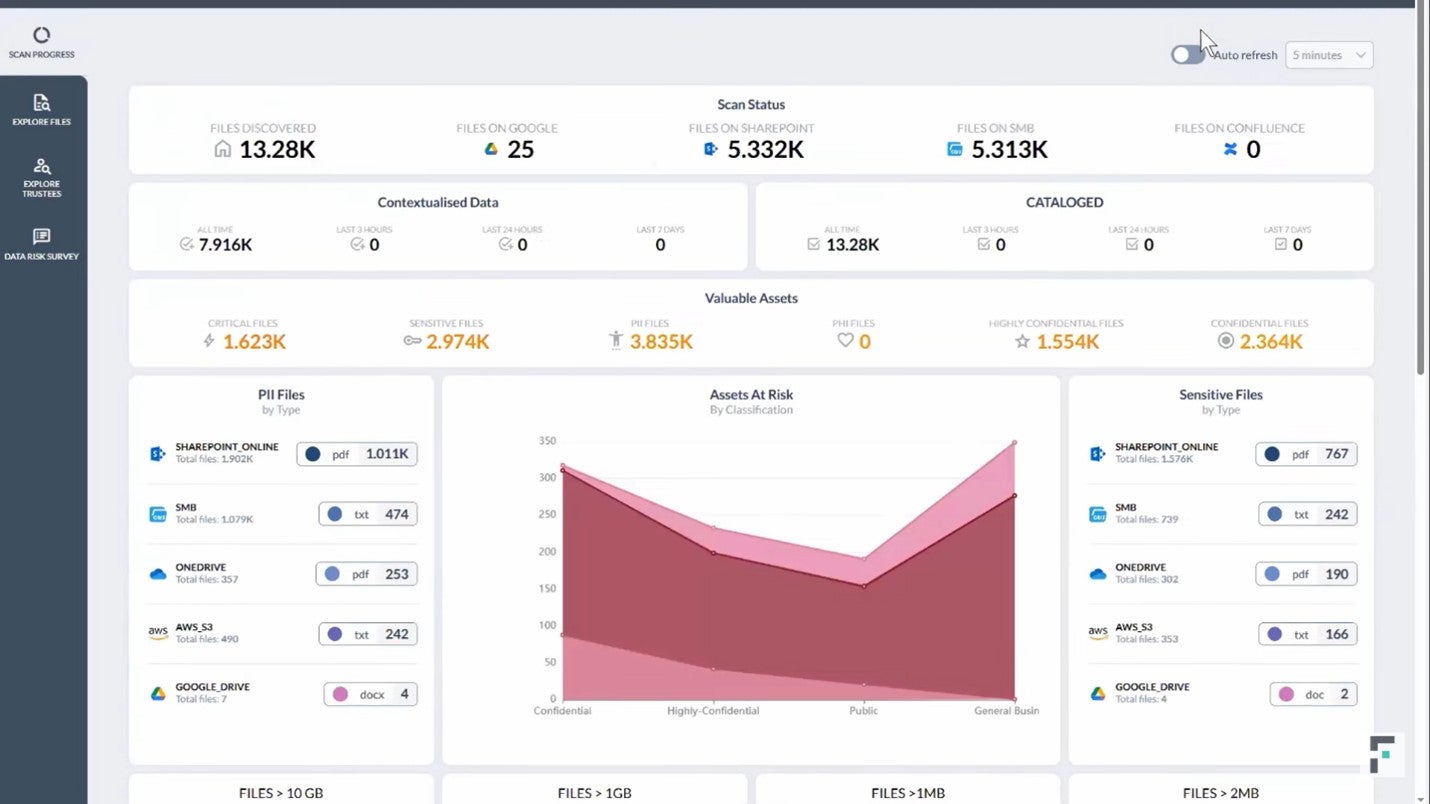
Fig. 1 - Forcepoint DSPM scanning dashboard
The user can view the results of the scan in a report format that is thoroughly customizable and interactive. In this view, admins can inspect permissions for all files and users, seeing which individuals have access to a file across the organization. This provides unprecedented visibility into dark data – the up to 80 percent of data stored by a typical organization that goes unused and often unknown – revealing files that may be redundant or over-permissioned.
Explore and fine-tune your scan results
For data classification, Forcepoint DSPM utilizes the AI Mesh, a highly networked classification architecture that uses an efficient GenAI Small Language Model (SLM). The AI Mesh determines whether a piece of data is sensitive and/or critical based on AI classifiers and data science capabilities such as:
- Deep neural network classifiers for sentiment analysis
- Light AI classifiers such as Bag of Words for determining topics
- Bayesian inference for predictive modeling of text
- Regex filters to delineate what text is classifiable
This advanced architecture enables the classification engine in Forcepoint DSPM to deliver outstanding accuracy. Using both AI and pattern matching, the solution first produces different classification labels for regulatory compliance purposes, then adds contextualized information about those files by breaking them down into categories and subcategories and by adding tags. Achieving persistent tagging through automation is a key contributor to helping a reactive security solution such as DLP to consistently prevent data breaches without returning time-wasting false positives.

Fig. 2 - Forcepoint DSPM pattern matching
In addition to sorting by categories and tags, admins can easily refine search results with advanced queries that the solution helpfully auto-completes. Beyond the pattern matching functionality, users can also set up detectors – alerts for certain parameters during a classification search. An admin can use one to search for keywords within the entire contents of a document or file or to find keyword hits within the file's pathname.
Admins can fine-tune the AI model behind the data classification by sending files back to the ML pipeline, confirming whether they were true positives. Another option is to send files back to the classification pipeline, where you can add Microsoft tags using Purview or persistent Forcepoint tags that will remain with the files even outside vendor-specific file ecosystems such as O365 and Google Cloud.
The whole package: Remediation, compliance, analytics
One of the most convenient features of Forcepoint DSPM is the ability to perform remediation activities directly from this report format. Admins can revoke improper permissions on the spot while viewing files, streamlining workflows and allowing for quick and decisive action to eliminate data risks.

Fig. 3 - Revoking permissions from Forcepoint DSPM's report view
Even this doesn’t come close to exhausting the capabilities of Forcepoint DSPM. Other key features include the Compliance Hub, where you can not only generate audit-friendly reports but also break down information about incidents that can be important for directing regulatory compliance activities.
Finally, the advanced analytics capabilities of Forcepoint DSPM allow you to generate dashboards to easily visualize the flow of data across your organization and throughout its entire lifecycle. For instance, admins can track the storage location of data to ensure that data sovereignty rules are being followed. These dashboards are highly customizable and can provide stakeholders with valuable, accessible insights into your organization’s stewardship of sensitive data.
Track and protect sensitive data throughout its lifecycle
Defensive solutions like Forcepoint Data Loss Protection (DLP) are critical for stopping data breaches and data exfiltration, but DLP works far more effectively when you have already discovered your data and leveraged AI Mesh to classify it. This makes it easy for DLP policies to correctly identify what types of data are about to leave the organization, reducing false positives and stopping data loss.
By organizing your data ecosystem with a solution that heavily leverages automation and simultaneously gives admins wide-ranging power for risk remediation, you can make the most of your resources and avoid the kind of oversights that lead to data breaches and regulatory non-compliance. You can finally combine Forcepoint DSPM with Forcepoint DLP and add Risk-Adaptive Protection to monitor user behavior and uncover insider risk, leading to a comprehensive security strategy that sees and protects sensitive data throughout every moment of its lifecycle.
Are you ready to try Forcepoint DSPM out yourself? Talk to an expert to set up your demo and learn how many tools are at your disposal to protect your sensitive and critical data.

Tim Herr
Read more articles by Tim HerrTim serves as Brand Marketing Copywriter, executing the company's content strategy across a variety of formats and helping to communicate the benefits of Forcepoint solutions in clear, accessible language.
 Executive Guide to DSPM: Visibility and Control over Sensitive DataRead the eBook
Executive Guide to DSPM: Visibility and Control over Sensitive DataRead the eBook
X-Labs
Get insight, analysis & news straight to your inbox

To the Point
Cybersecurity
A Podcast covering latest trends and topics in the world of cybersecurity
Listen Now