12K+ customers couldn't be wrong










































Perimeter Defense isn’t Enough. Secure Data Everywhere with Pinpoint Precision.
Our Data Detection & Response (DDR) software uses AI-powered classification and continuous monitoring for dynamic detection and prevention of data exfiltration. Don’t just identify risks; prioritize and accelerate remediation.
Forcepoint DDR is perfect for helping companies:
Detect and respond to potential data breaches and insider threats
Dynamically protect sensitive data in use
Get extensive visibility across clouds and endpoints
Save money through breach prevention


Explore Forcepoint DDR
See our Data Detection & Response (DDR) software in action. Get a tour of the platform and learn how it protects structured and unstructured data.
Why Use a Data Detection and Response Solution?
Classify with Confidence
Enhance data context by using AI Mesh to understand its unique relevance and sensitivity.
Detect Threats Early
Reduce mean time to detection with continuous monitoring of file sharing, renaming and movement.
Cover Endpoint and Cloud
Extend visibility and enforcement to cloud and endpoint for extensive coverage.
Limit False-Positive Alerts
Prioritize alerts based on severity to improve meantime to response.


Stay Ahead of Risk
A data risk assessment proactively discovers threats to your data, whether it's unclassified sensitive files or overpermissioned users. Get a free data risk assessment with Forcepoint to see DSPM in action and learn how safe your data is.


Watch Video
Pinpoint Accuracy and Transparent Reporting
Enda Kyne, CTOO at FBD Insurance, says that DSPM and DDR has been embraced by his IT security and data protection teams for their ability to control critical data and report activity to regulators.
Why Forcepoint Data Detection & Response?
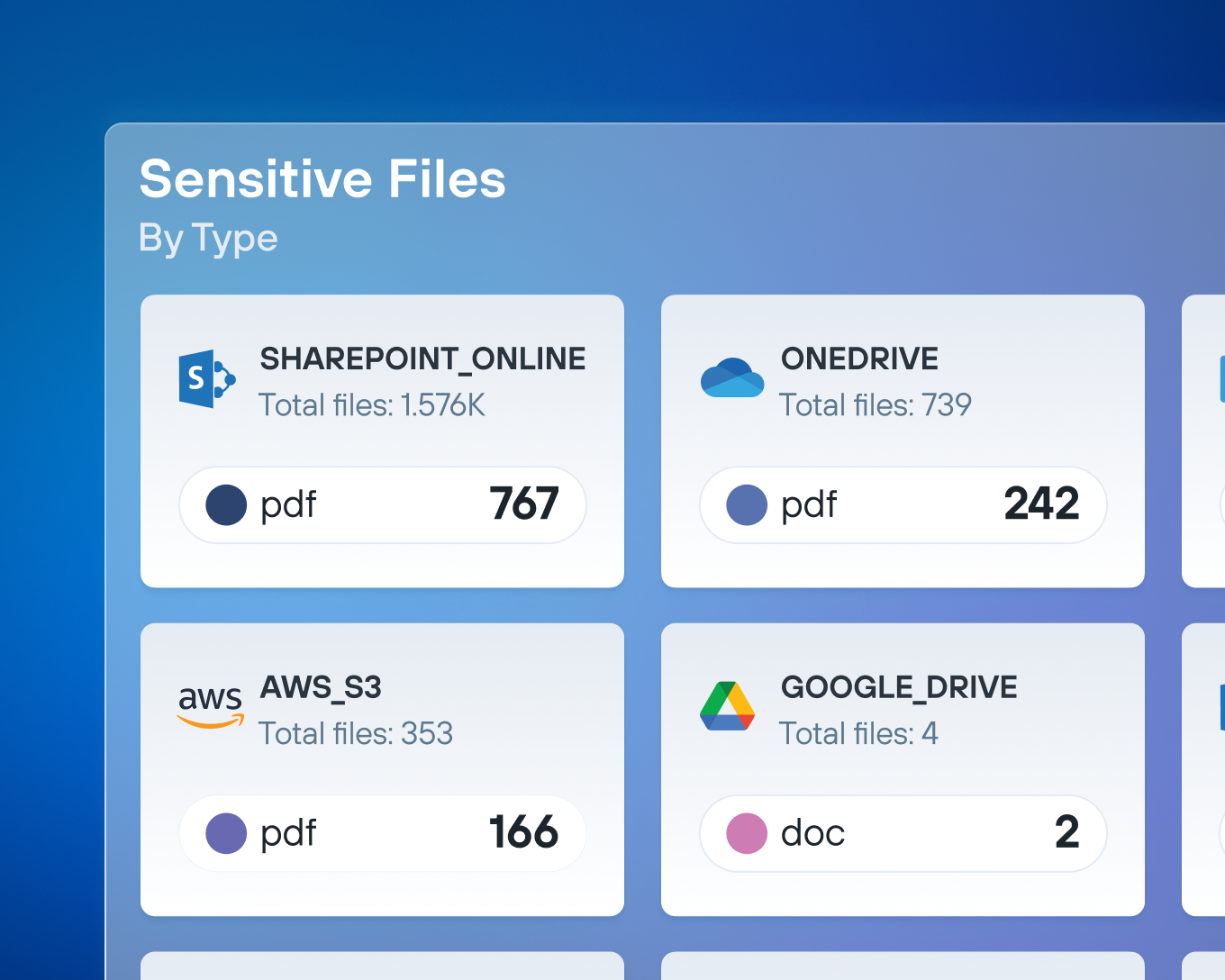


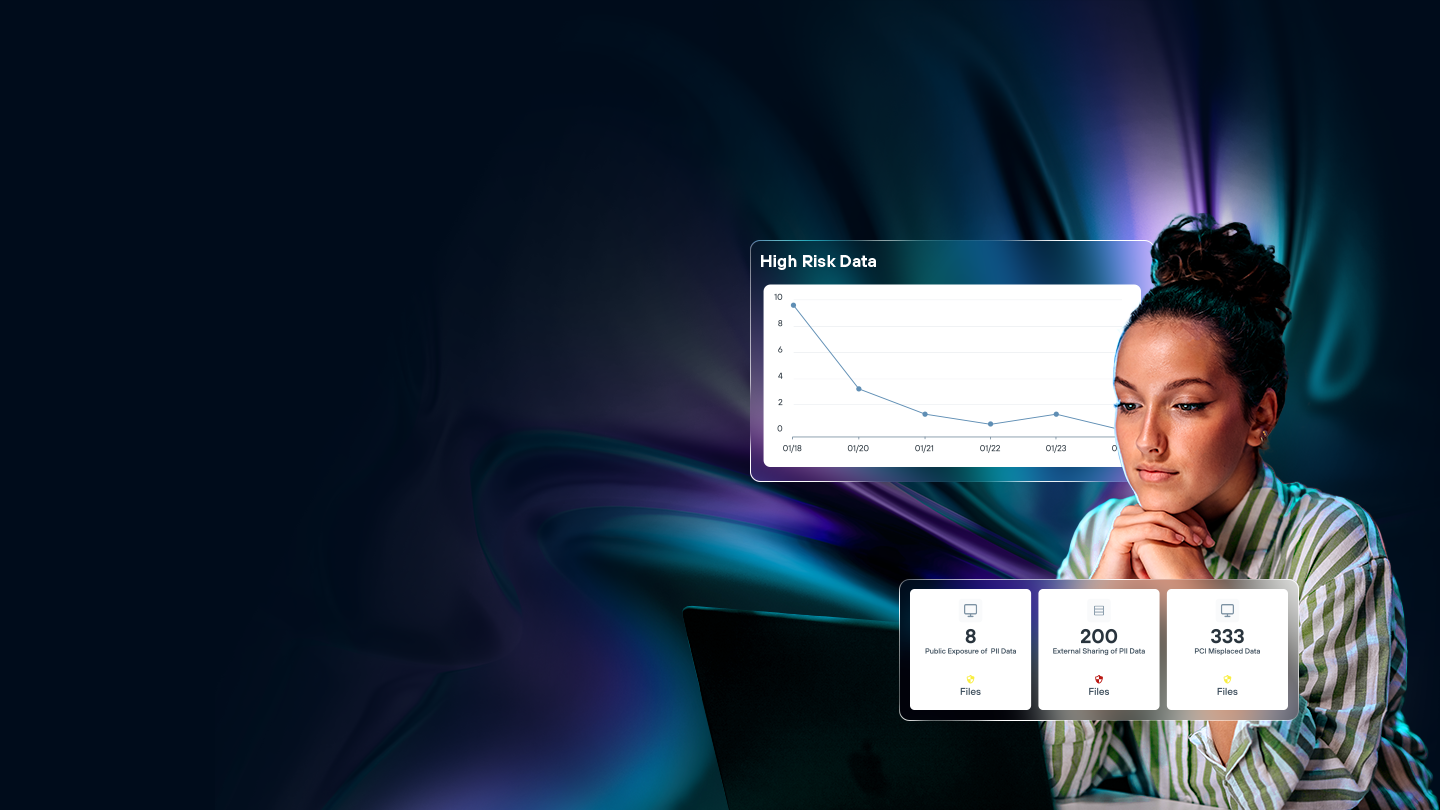
Monitor data activities 24/7 across your entire digital landscape. DDR tracks file access patterns, sharing behaviors, and data movements in real-time, alerting security teams to activities that could signal insider threats or compromise attempts before sensitive data leaves your control.

The classification engine that fuels Forcepoint DDR uses our proprietary AI Mesh technology to provide highly precise classification. AI Mesh uses a blend of a GenAI small language model, neural network classifiers, predictive AI and other data components to improve accuracy.

Forcepoint DDR can be configured as an add-on to Forcepoint DSPM. Together, they provide continuous identification, classification and threat prevention, with coverage that extends across the organization.
What DDR Customers Are Saying
What DDR Customers Are Saying



Frequently Asked Questions
What are the business benefits of DDR?
Forcepoint DDR helps prevent costly data breaches by detecting real threats earlier and focusing teams on the highest-risk events, which reduces incident impact, investigation time, and overall security operations cost.
It also increases confidence in digital transformation – cloud adoption, remote work, and AI/GenAI use – by providing continuous visibility into sensitive data and clear reporting that supports executive, customer and regulatory requirements.
Why is DDR important?
Forcepoint Data Detection and Response (DDR) is important because it continuously monitors how sensitive data is actually used across endpoints and cloud environments so you can spot and stop indicators of a breach while they’re happening, not months later. Traditional controls often leave a “visibility gap” around data-in-use. DDR closes that gap with real-time monitoring, AI-powered classification and automated responses to suspicious activity. It combines context from data, user behavior and permissions to reduce attacker dwell time, mitigate insider threats and prevent data exfiltration.
How does DDR detect threats or risky behavior?
Forcepoint DDR detects threats by continuously analyzing data events such as reads, views, creations, permission changes, renaming and sharing activities. It rescans items when significant changes occur and evaluates for anomalies and policy violations that indicate misuse, insider threats, compromised accounts or emerging exfiltration patterns.
Forcepoint AI Mesh adds context to distinguish normal business use from risky actions, then generates prioritized alerts and recommended or automated remediation steps to help security teams respond before data leaves your control.
How fast can DDR detect data exfiltration attempts?
DDR is designed for continuous, near-real-time monitoring and alerting. It tracks file access, movement and sharing 24/7 and raises alerts as soon as relevant risky events are observed and evaluated.
How does DDR help organizations stop data loss and address vulnerabilities?
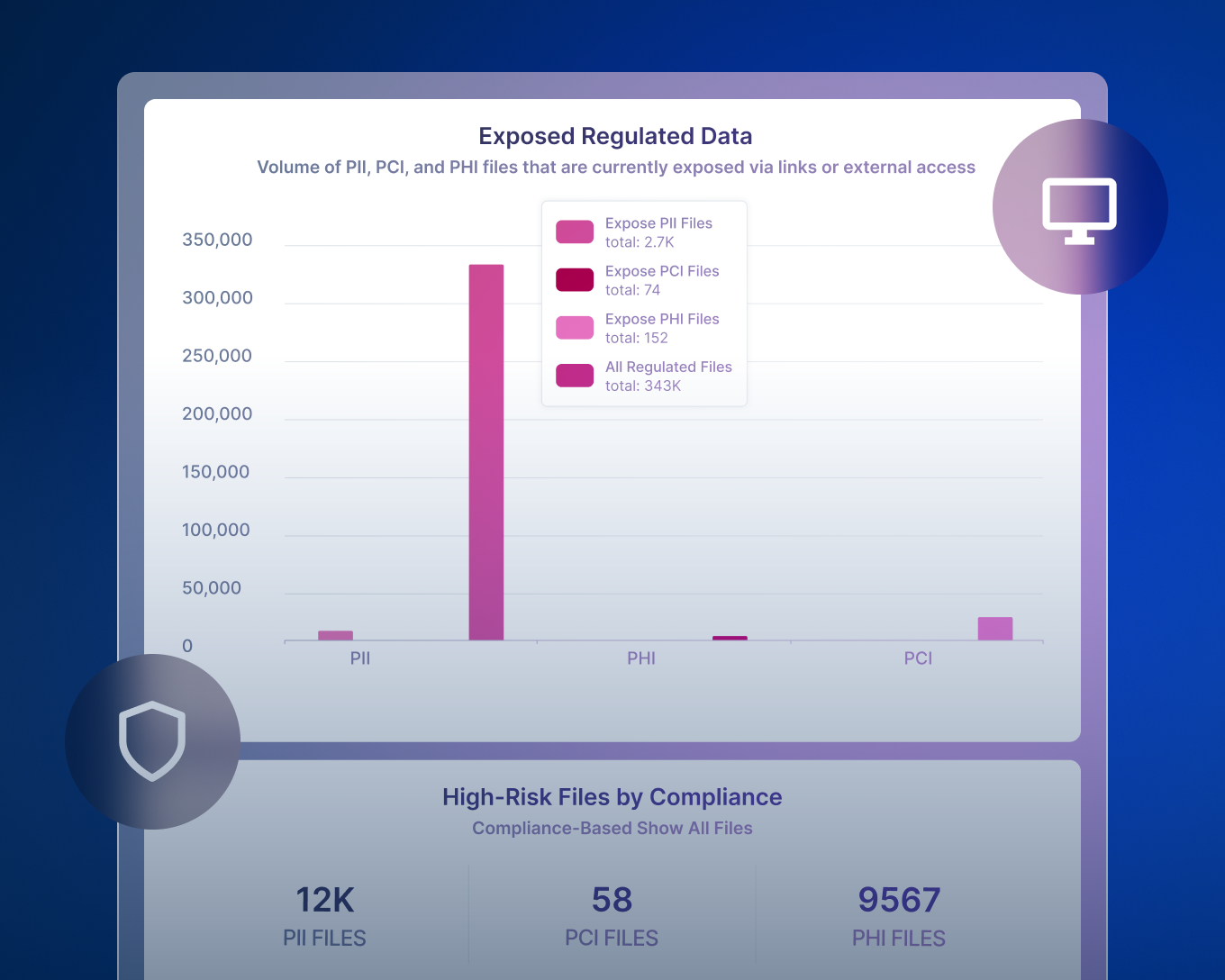
Forcepoint DDR supports pre-defined templates to detect exposure to sensitive data like PII, PCI, and PHI. These templates simplify audits and compliance reporting, with continuous monitoring and detailed data histories.
Can DDR prevent data leaks in cloud apps?
Yes. Forcepoint DDR extends monitoring and protection to supported cloud and SaaS environments, using AI-powered classification and continuous analysis of file activities (such as uploads, shares, and permission changes) to detect and help prevent data exfiltration.
Does DDR use AI in its threat-detection capabilities?
Yes. The classification system in Forcepoint DDR is powered by AI Mesh, which provides high accuracy, a better understanding of context, and risk scores across monitored environments. This AI-native approach improves detection quality (fewer false positives, better prioritization) and enables automated or guided responses to suspicious data activity, making DDR materially more effective than static rule-only monitoring.
What types of data does DDR monitor and protect?
Forcepoint DDR monitors both structured and unstructured data, with specific focus on sensitive information such as PII, PHI and PCI data, as well as business-critical intellectual property. It tracks data across supported cloud and endpoint sources, following how files and records are created, accessed, modified, renamed, shared, or deleted. Using its proprietary AI Mesh data classification, it continuously identifies and prioritizes at-risk data wherever it resides.
How does Forcepoint DDR integrate with other security tools?
Forcepoint DDR is an important add-on to Forcepoint DSPM solution, enabling continuous monitoring of data in use. Pairing Forcepoint DSPM and DDR with Forcepoint DLP creates a comprehensive data security ecosystem, protecting data wherever it resides, how it is accessed or how it changes over time. Forcepoint DDR also seamlessly integrates with SIEM and SOAR solutions through webhooks to improve incident response and threat management.
What does DDR solve that DLP and SIEM don’t do?
Forcepoint DDR focuses on data-in-use and data behavior, delivering continuous monitoring, rich context and dynamic response where traditional DLP and SIEM have blind spots. DLP is optimized to enforce policies on data-in-motion (email, web, endpoints, etc.), and SIEM aggregates logs and alerts from many systems. DDR adds deep, AI-driven understanding of sensitive data and its lineage plus targeted response actions across clouds and endpoints. DDR enhances DLP and SIEM, augmenting them with highly accurate, context-centric intelligence and automating remediation when suspicious activities begin to take place. In combination, the three tools form the foundation for an effective data security strategy.
How does DDR support compliance and auditing?
Forcepoint DDR supports compliance by continuously monitoring exposure of regulated data such as PII, PHI, and PCI, using predefined detection templates and AI-driven classification aligned to common privacy and industry frameworks. This ensures faster identification of non-compliant data handling across monitored sources.
For auditors and regulators, Forcepoint DDR maintains detailed histories of data activities and risk events, enabling transparent reporting on who accessed what, how data moved, and which remediation actions were taken. This directly supports audits for GDPR, HIPAA, PCI DSS, CCPA and similar mandates.
How does Forcepoint DDR support compliance with global data protection regulations?
DLP uses multiple tools to identify sensitive information within an IT environment, monitor data flow in and out of the organization and block sensitive data from leaving the organization based on security policies.