
12K+ customers couldn't be wrong










































Get Visibility and Control Over Sensitive Data
Shine a light on dark data with extensive data discovery and highly accurate classification.
Forcepoint DSPM software uses proprietary AI Mesh technology to identify and categorize high-risk data, displaying real-time insights including scan status, performance metrics and audit log visuals.
It's a perfect solution if your security teams struggle with:
Large amounts of shadow data
Over-permissioned data
GenAI data leakage risks
Unidentified data locations
Forcepoint DSPM Software Leads the Pack
Forcepoint is the only Data Security Posture Management vendor that uses AI Mesh technology to deliver highly accurate data classification. Read the full comparison chart to learn why organizations trust the leading data security provider to discover and catalogue data and remediate risk at scale.
20%
40%
60%
80%
100%
Forcepoint
Traditional Vendor
Data Governance Vendor
Why Forcepoint is a Top-rated DSPM Vendor
Improve Data Visibility
Gain complete visibility into structured and unstructured data across the cloud and on-premises environments to track and manage sensitive data wherever it resides.

Discover and Classify with AI
Utilize advanced AI Mesh technology integrated with established DLP classifier policies to achieve plug-and-play protection with minimal configuration, reduce false positives and enhance incident alert accuracy.

Proactively Remediate Risk
Actionable insights enable you to manage permissions, move misplaced data and address data sovereignty, access and duplicate or ROT data issues.

Automate Compliance Management
Simplify compliance processes with automation to ensure consistent and continuous alignment with evolving regulations, reducing manual effort.



Pinpoint Accuracy and Transparent Reporting
Enda Kyne, CTOO at FBD Insurance, says that DSPM and DDR has been embraced by his IT security and data protection teams for their ability to control critical data and report activity to regulators.
Strengthen Your Data Security Posture




Rapidly and precisely identify sensitive data-at-rest with self-improving AI Mesh technology paired with proven DLP classifier policies for maximum efficiency.

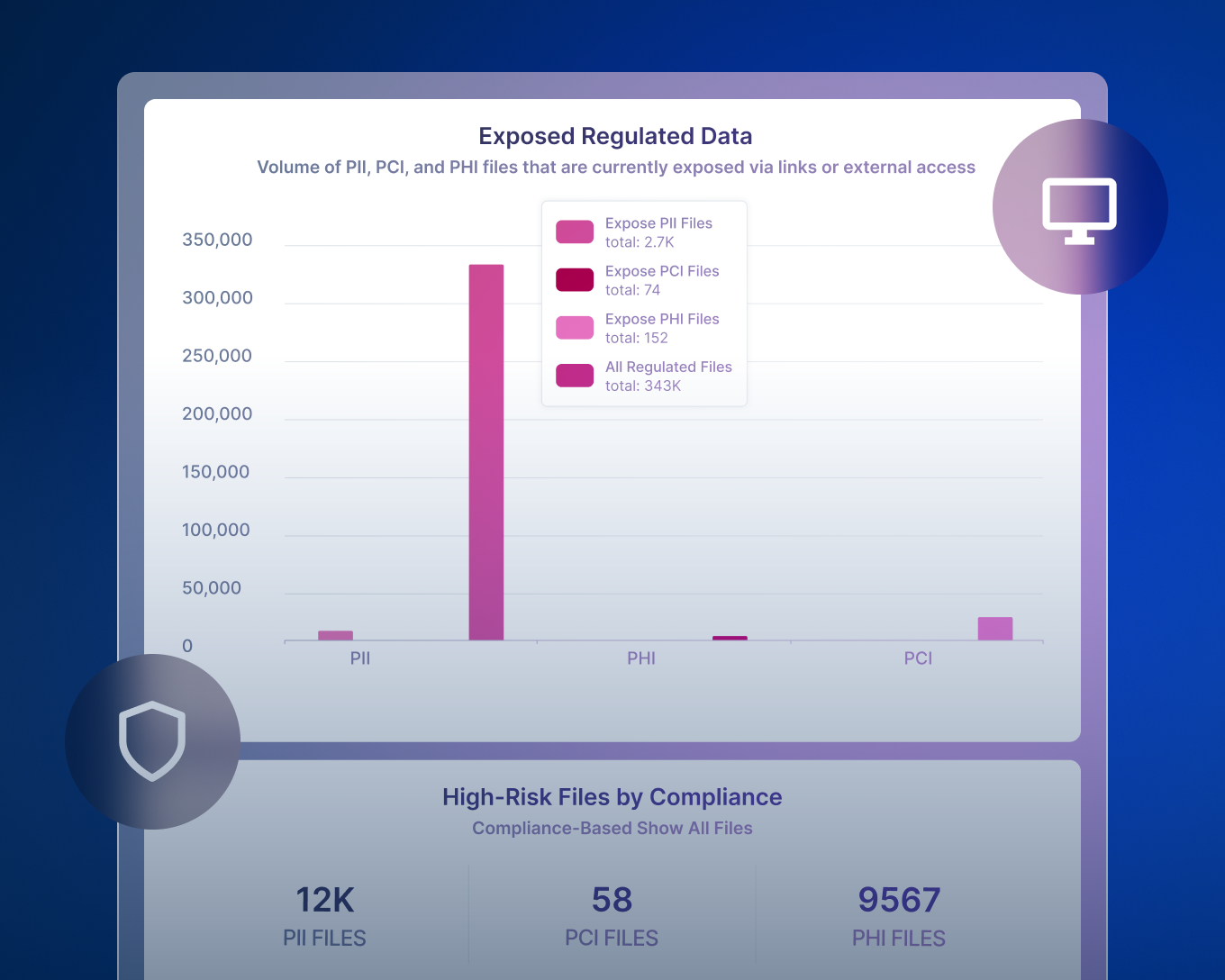
Extend visibility and control over all your regulated data, eliminate gaps and generate automated reports to demonstrate compliance.

Gain a centralized view of your data and enforce the Principle of Least Privilege across cloud, SaaS and on-prem systems for effective governance.


Stay Ahead of Risk
A data risk assessment proactively discovers threats to your data, whether it's unclassified sensitive files or over-permissioned users. Get a free data risk assessment with Forcepoint to see AI-Native DSPM in action and learn how safe your data is.
Ensure Safety of Sensitive Data



Ability to integrate DLP, AI-Native DSPM and DDR for data discovery, classification, protection and remediation.

Provides effective risk reporting with a real-time dashboard giving instant visibility and actionable insights into ROT (redundant, obsolete, trivial) data, over-permissioned data, data sovereignty issues and other data security posture challenges.

Offers visibility and control into data readiness for all GenAI applications. It is also able to secure Copilot and ChatGPT Enterprise usage.
What Real Customers Are Saying
What Real Customers Are Saying
"As part of Forcepoint’s broader data security ecosystem, DSPM has integrated seamlessly with our existing solutions. It’s an essential component of our overall data security strategy."
Indonesia Financial Group (IFG)
Analyst recommended.
User approved.
Forcepoint is consistently ranked among the top Data Loss Prevention software solutions and data security software providers by users and industry analysts.
Forcepoint has been named a Leader in the IDC MarketScape: Worldwide DLP 2025 Vendor Assessment.
Forcepoint named the 2024 Global DLP Company of the Year for the second consecutive year by Frost & Sullivan.
Forcepoint recognized as a Strong Performer in The Forrester Wave™: Data Security Platforms, Q1 2025.
Implement Data Security Posture Management Best Practices
Frequently Asked Questions
What is Data Security Posture Management (DSPM)?
Data Security Posture Management is a security solution that continuously discovers where sensitive data lives, how it’s classified and who can access it across cloud, SaaS and on-prem environments. Forcepoint’s AI-native DSPM follows this same model: it continuously inventories structured and unstructured data, uses AI Mesh technology to accurately classify that data across file storage, cloud apps and on-prem locations, and assesses whether any of that data is at risk through a variety of lenses. Forcepoint DSPM helps increase productivity, cut costs, reduce risk and streamline compliance by turning posture from a periodic audit into a live-running view of data risk.
How do DSPM solutions work?
Most DSPM platforms follow a recurring lifecycle: discover data (structured and unstructured across multiple clouds and on-prem), classify it by sensitivity and business context, assess and prioritize risks (such as overprivileged access or mislocated data), remediate misconfigurations or unsafe access, and then monitor continuously to keep posture current. Forcepoint DSPM implements this with AI Mesh, an AI classification architecture using small language models and deep neural networks.
Forcepoint DSPM will scan integrated data sources, identify and categorize high-risk data, and recommend next steps for remediation so the team can adjust permissions, move misplaced data, clean up Redundant, Obsolete or Trivial (ROT) data and fix sovereignty issues instead of stopping at reports. Recent updates extend Forcepoint DSPM beyond files into enterprise databases and data lakes, so the same discovery, classification and adaptive enforcement model now covers both structured and unstructured data in a single, unified platform alongside Forcepoint DDR and DLP.
How does DSPM software’s data discovery capabilities work?
DSPM continuously discovers data across cloud, network and on-premises storage to uncover and catalog every piece of data your organization has. Finding sensitive data is the crucial first step in protecting it. DSPM solutions scan your entire data ecosystem such as:
- Cloud platforms (AWS, Azure, GCP)
- SaaS applications (Microsoft 365, Salesforce)
- On-premises storage and databases
Modern DSPM software maintains continuous visibility as data moves and changes through built-in functionality or solution integrations.
What data classification and risk assessment abilities does a DSPM solution provide?
A mature DSPM solution delivers a chain of capabilities:
- Data discovery and AI-powered classification: automated scanning of cloud, SaaS, endpoints and on-prem stores, using finely tuned AI to accurately classify structured and unstructured data by sensitivity and business purpose, with tunable models to reduce false positives.
- Data risk assessment plus risk analysis and prioritization: building an inventory of sensitive data, then scoring risk based on exposure, over-permissive access and business impact so teams focus on the most critical datasets first; Forcepoint uses risk scoring and financial-impact estimates to prioritize mitigation.
- Access governance: surfacing who has access to which data, highlighting public or external sharing, inactive accounts and overshared folders, with deep visibility into permissions via directory integrations.
- Compliance and reporting: generating dashboards, audit trails and framework-aligned reports (for regulations like GDPR or HIPAA) that map regulated data, document controls and simplify audits; Forcepoint adds policy templates, automated reporting and explainable AI classification to streamline demonstrating compliance across hybrid environments.
How does a DSPM platform help organizations manage and remediate risk?
Identifying issues without resolution creates little value. Modern DSPM platforms bridge this gap with customizable controls that adapt to your organization's unique needs and challenges. These controls include permissions management to implement the Principle of Least Privilege (PoLP), ensuring users only access files required for their tasks and addressing over-permissioned or publicly accessible data. Additional capabilities include data mapping to properly categorize sensitive information, mislocated data remediation to address files stored in inappropriate repositories and data archiving/deletion workflows for managing at-risk files past retention periods or classified as ROT (redundant, obsolete, trivial).
How does reporting and analytics work within DSPM software?
DSPM solutions include reporting and analytics tools that provide visibility into an organization's overall data security status. These reporting capabilities typically feature dashboards showing where sensitive data exists across environments, highlighting specific risk factors such as ROT (redundant, obsolete, trivial) data, over-permissioned files, mislocated information and duplicated content. Security teams can use these insights to track metrics over time and prioritize remediation efforts where they'll have the greatest impact.
Is Forcepoint DSPM deployed on-premises or in the cloud?
DSPM solutions offer flexible implementation options:
- Cloud-native SaaS for rapid deployment
- Hybrid models for sensitive environments
- On-premises for control over data sovereignty
- Agentless architectures to minimize overhead
Most enterprises start with their most critical data repositories and expand coverage incrementally.
How does Forcepoint DSPM use AI and automation?
Automation enables continuous, large-scale data discovery and scanning across enterprise environments. Organizations can now automatically classify data in real-time as it's created, moved or modified—eliminating the delays and gaps inherent in manual reviews. Artificial intelligence's primary value lies in delivering highly accurate data classification while reducing false positives. AI brings the precision needed to confidently distinguish between truly sensitive data and benign information that might trigger traditional rule-based systems. For DSPM solutions to confidently incorporate these capabilities, modern solutions must handle a wide range of file types, from PDFs to video, as well as understand an even broader array of data fields to assign correct classifications and adjust for compliance requirements. This includes leveraging GenAI capabilities, deep neural network classifiers and other predictive AI technologies working together.
What are the key benefits organizations could get from implementing a DSPM platform?
The benefits of Data Security Posture Management can boil down to four outcomes:
- Increase productivity
- Cut costs
- Reduce risk
- Streamline compliance
Does DSPM integrate with other security technologies?
DSPM rarely operates in isolation. Most organizations integrate it with complementary security technologies to create a comprehensive data protection strategy. The insights DSPM software provides about data location, sensitivity and risk naturally enhance other security tools such as:
- Data Detection and Response (DDR)
- Data Loss Prevention (DLP)
- Cloud Access Security Broker (CASB)
- Identity and Access Management (IAM)
- Cloud Security Posture Management (CSPM)
How does DSPM differ from legacy data classification tools?
Unlike traditional tools that work with known data repositories using predefined rules, DSPM continuously discovers both known and unknown data across environments, leveraging AI for more accurate classification and providing context about access patterns and security controls.
How does DSPM help assess security posture?
Data Security Posture Management (DSPM) assesses security posture by continuously discovering where sensitive data lives (cloud, SaaS, on-prem), classifying it by sensitivity and mapping who has access to it.
Forcepoint DSPM uses its AI Mesh engine plus broad connectors to inventory structured and unstructured data. It highlights overexposed files, ROT data and risky permissions, and correlates them into a data risk assessment.
It then provides high-performance monitoring and analytics to show how much sensitive data is at risk, which locations and business units drive the most exposure, and how changes over time impact overall data risk. These insights are surfaced through detailed dashboards and reporting, giving security and compliance teams a current, measurable view of their data security posture instead of point-in-time audits.
What is the difference between SSPM and CSPM and DSPM?
CSPM (Cloud Security Posture Management) focuses on cloud infrastructure: configurations, network controls, identities, and platform services. It finds and helps fix misconfigurations in IaaS, PaaS and SaaS environments, not the contents of the data itself.
SSPM (SaaS Security Posture Management) focuses on SaaS apps: security settings, access and integrations across services like Microsoft 365, Salesforce and more.
DSPM (Data Security Posture Management) focuses specifically on the data—discovering, classifying, and assessing risk around sensitive information wherever it is stored. It answers, “what data do we have, where is it, who can access it and how risky is that exposure?”
Does Forcepoint DSPM have real-time monitoring and risk detection?
Yes. Forcepoint DSPM provides real-time or high-frequency risk assessment as it scans, updating dashboards with exposure levels and leveraging an advanced alerting system to automatically flag anomalies and potential breaches.
How does DSPM enhance cloud security?
DSPM enhances cloud security by giving full visibility into sensitive data stored across cloud storage, SaaS platforms and databases. It shows exactly what data exists, how sensitive it is, where it resides and how it’s shared.
Forcepoint DSPM scans major cloud providers and identity sources to uncover overexposed data, excessive permissions and mislocated sensitive content that traditional cloud tools miss. With this context, security teams can enforce least-privilege access in the cloud, prioritize remediation based on real business and regulatory impact, and integrate DSPM findings with DLP and other controls.
What are the benefits of using DSPM in cloud security?
Using DSPM in cloud environments delivers concrete outcomes: reduced data exposure (through overexposure detection and permission cleanup), fewer blind spots across multi-cloud and SaaS, and better protection for IP and regulated data.
Forcepoint AI Mesh improves the classification accuracy of Forcepoint DSPM, which directly cuts false positives and helps teams focus on real risk.
It also improves operational efficiency via automation, integrated dashboards and reporting. It shortens investigation and remediation cycles, lowers storage and governance costs by addressing ROT data and addresses compliance readiness for audits and data protection regulations.
Does DSPM help with identity threat detection and response?
DSPM is not an Identity Threat Detection & Response (ITDR) platform, but Forcepoint DSPM does detect identity-related risks tied to data. It maps which users and groups can access sensitive files, highlights over-permissioned or high-impact “risky users,” and surfaces suspicious access patterns via analytics and alerts.
These insights let security teams quickly investigate potential identity misuse (e.g., a user with excessive access to critical data) and take targeted actions such as revoking access, tightening sharing, or triggering workflows in existing security tools – strengthening identity-centric data protection without guessing.
How does DSPM detect and evaluate sensitive data exposure?
Forcepoint DSPM uses connectors to scan cloud and on-prem data stores at scale, then applies AI Mesh classification and configurable detectors to identify sensitive data (PII, PCI, PHI, IP, etc.) based on content and context.
It then evaluates exposure by analyzing sharing settings and permissions to flag data that is public, externally shared, overshared internally, mislocated, or associated with risky users, and quantify that risk within dashboards and reports so teams can prioritize remediation.
How does DSPM simplify compliance reporting?
Forcepoint DSPM centralizes evidence needed for regulations like GDPR, HIPAA and other privacy and sovereignty requirements by continuously documenting where regulated data resides, how it’s protected and who can access it. Its reporting function and analytics suite show compliance readiness and data risk across popular frameworks.
What dashboards are included in Forcepoint DSPM for compliance teams?
The Forcepoint DSPM Analytics suite includes predefined dashboards such as overexposure analysis, ransomware exposure analysis, critical data duplication, risky user detection, data retention, misplaced data, data risk assessment and incident tracking for data control violations.
Compliance teams can also create custom dashboards using built-in widgets (counters, charts, tables, incident views, etc.) driven by DSPM’s query language, and export these views as reports to allow them to tailor oversight to specific regulations, business units or data categories without custom development.



